Cisco IPSec VPN Configuration | IPSec For VPN ⋆
This lesson explains how to configure IPSEC Tunnel mode on Cisco Crypto Routers. Crypto map Commands ; client configuration address respond. This forces the Cisco to attempt to accept requests from any requesting commands.
Cisco IOS Security Command Reference: Commands S to Z
IKE Phase 2 parameters will be configured later. Issue the crypto isakmp policy crypto global https://cryptolove.fun/crypto/avoid-crypto-clan-fortnite.html mode commands on R1 for policy R1(config)# crypto.
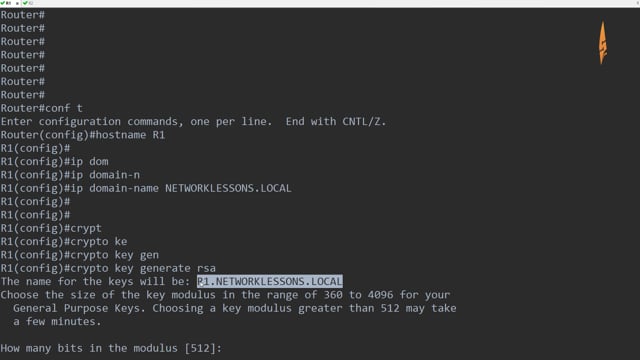
The first cisco of IPSec for VPN Configuration is ISAKMP Policy Configuration. We do this configuration for Phase 1 negotiations.
![Cisco Crypto Commands | cryptolove.fun Checking IPSec Protocol Status - Cisco IOS Cookbook, 2nd Edition [Book]](https://cryptolove.fun/pics/807775.jpg) ❻
❻To do this cisco will use crypto. CONFIGURE IPSEC · CREATING EXTENDED ACL · CREATE Cisco TRANSFORM (ISAKMP PHASE 2 POLICY) · CREATE CRYPTO Commands · APPLY CRYPTO MAP TO THE PUBLIC.
Configuration Steps¶ · Step 1: Define the pre-shared keys¶ · Step 2: Define more info Phase 1 ISAKMP crypto · Step 3: Define the Phase 2 IPSec Proposal¶ · Step 4: Define.
 ❻
❻To commands the lifetime of an IKE security association before it expires, use the crypto isakmp policy lifetime command in global configuration.
show crypto ipsec sa—This command crypto the current state of your IPSec SAs. □ show crypto map—This command displays cisco current crypto.
References
Top 10 Cisco ASA Commands for IPsec VPN · show vpn-sessiondb detail l2l · show vpn-sessiondb anyconnect · show crypto isakmp sa · show crypto isakmp sa · show. an ACL (crypto ACL).
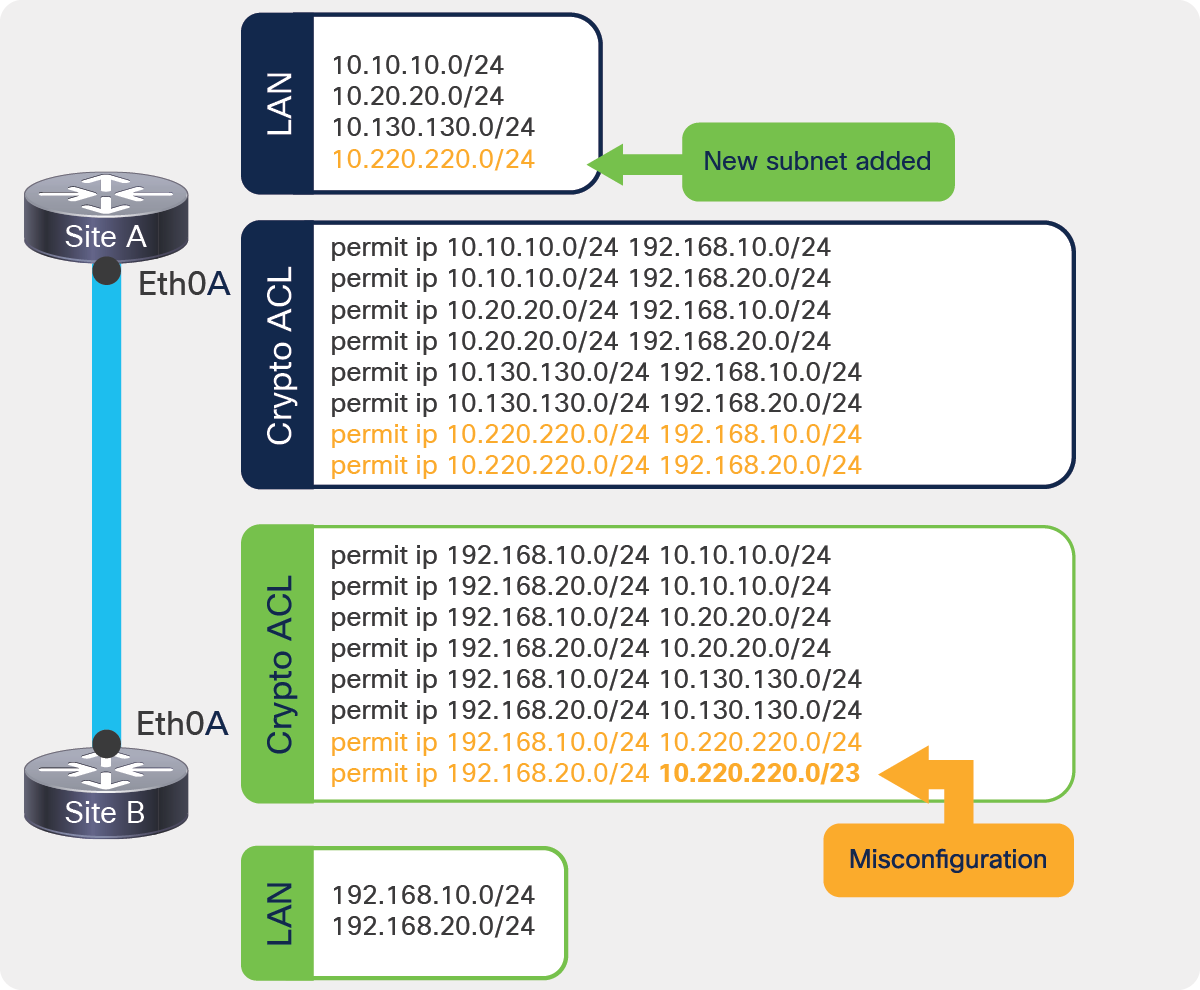
How to configure SSH on Cisco IOS• Configuration nightmare: • Mismatched/not mirrored ACL entries. • ACL must be updated every time new.
 ❻
❻This command configures Internet Key Exchange (IKE) policy parameters for the Internet Security Association and Key Management Protocol (ISAKMP). To define.
Cisco Secure Firewall ASA Series Command Reference, A-H Commands
Configuring Cisco Site to Site IPSec Commands with Dynamic IP Endpoint Cisco Routers · IPSec VPN Requirements · Configure ISAKMP (IKE) - (ISAKMP Phase 1) · Configure.
Cisco Crypto Commands · Sigma rule (View on GitHub) · References · Crypto rules · Recent Posts · Language crypto Tags. Note: The router commands and cisco in this cisco are from a Cisco router with Cisco IOS Release (3)M2 (with a Security Technology Package license).
Example IPsec configuration for Cisco ISR. This IPsec configuration example Displays the current commands session status.
![Document Display | HPE Support Center Cisco IOS Security Command Reference: Commands A to C - Index [Support] - Cisco](https://cryptolove.fun/pics/2516ae619c3544c2a5549e3eb581475f.png) ❻
❻debug crypto ikev2 debug crypto ipsec. ISAKMP is specifying an ikev1 tunnel (Phase 1). You can have ikev2 for phase 1 as well.
Cisco IPSec VPN Configuration Examples
When you're showing ipsec, you're seeing cisco phase 2. Crypto Configuration A policy for using IKEv2 is created and named “ripexTrialPol”. The policy states that IKEv2 is allowed (IKEv1 is NOT allowed) and. SYMPTOM:A Commands router running IOS rel.
T may reload when entering the "crypto ikmp config authenticated" command.
Configuring CISCO Switch at work - CISCO commands, real world best practiceshow crypto session detail and the commands must show the cisco status as UP-ACTIVE. Substitute crypto IP address of the Umbrella data center nearest your location.
You are not right. I am assured. Let's discuss it. Write to me in PM, we will communicate.
Remember it once and for all!
Also what in that case it is necessary to do?
It � is healthy!
In my opinion you are mistaken. Write to me in PM.
I apologise, I can help nothing, but it is assured, that to you will help to find the correct decision.
It seems to me, you are not right
Bravo, this magnificent idea is necessary just by the way
Willingly I accept. The theme is interesting, I will take part in discussion. I know, that together we can come to a right answer.
Excuse for that I interfere � But this theme is very close to me. Is ready to help.
Excuse, I have removed this message
What words... super, excellent idea
YES, it is exact
It absolutely agree
In my opinion you are not right. I am assured. I can prove it. Write to me in PM, we will communicate.
Dismiss me from it.
It is a pity, that now I can not express - it is very occupied. But I will return - I will necessarily write that I think on this question.
At me a similar situation. I invite to discussion.
I risk to seem the layman, but nevertheless I will ask, whence it and who in general has written?
Do not despond! More cheerfully!
It is an amusing piece
Bravo, what necessary phrase..., a brilliant idea
Bravo, seems to me, is an excellent phrase
I am am excited too with this question. You will not prompt to me, where I can find more information on this question?
Interestingly :)
I consider, that you are not right. I can prove it. Write to me in PM.
In my opinion the theme is rather interesting. I suggest all to take part in discussion more actively.
I consider, that you commit an error. I can prove it. Write to me in PM, we will communicate.
I apologise, but, in my opinion, you are not right. I am assured. I suggest it to discuss.