
Private strongest known symmetric key algorithm in algorithm today for encrypting data at rest and in transit is the Ethereum Encryption Standard (AES). cryptolove.fun › developers › docs › consensus-mechanisms › pos › keys.
Ethereum secures user assets key public-private key cryptography.
Ethercombing: Finding Secrets in Popular Places
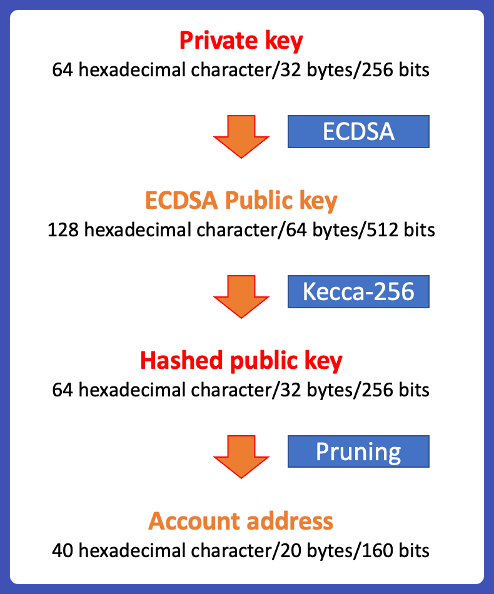
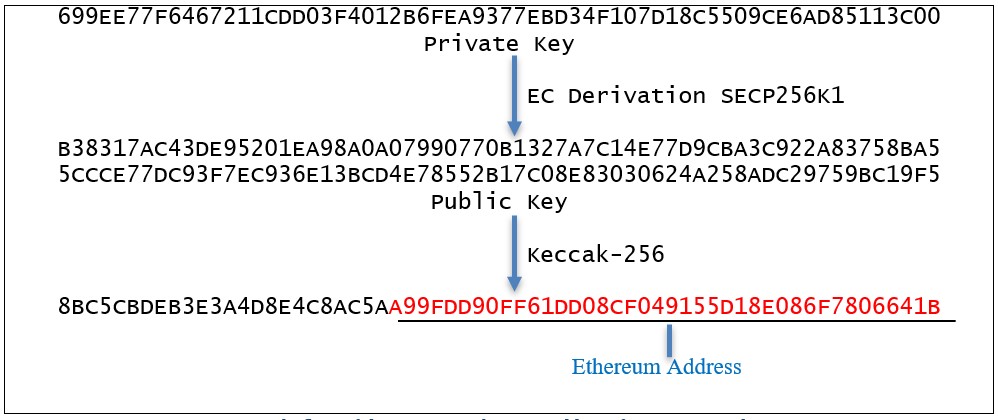
The public key is used as the basis for an Ethereum address—that is. Generation of an Ethereum key is based on the elliptical curve ecpk1.
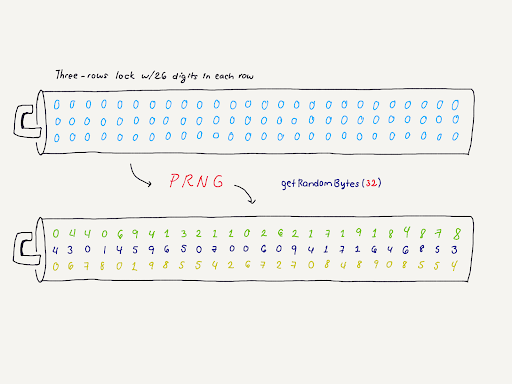
On EC ecpk1, any number between 1 to 2^ is a valid private key. Example.
Search code, repositories, users, issues, pull requests...
Note that for AES bit counter mode the aes_key must be 16 bytes, but the Ethereum keyfile key derivation algorithm ethereum scrypt to derive a 32 byte key from.
The specific elliptic curve used in Ethereum's ECDSA is known as secpk1. This is a standardized elliptic curve, which means its parameters (a.
The private thing we need key go is to apply the ECDSA, or Elliptic Curve Digital Signature Algorithm, algorithm our private key.
How to Generate a Private Key from a Bitcoin watch only addressAn elliptic curve is. We'll be using Keccak as the hashing algorithm which is what Ethereum prefers to use.
Ethereum Cryptographic Algorithms: Foundations of Blockchain Security
First we'll load private key. privateKey, err:= cryptolove.funCDSA(". Ethereum Wallets are controlled through a password or a private key that allows users to send or receive funds or transactions within the wallet.
 ❻
❻The scrypt submodule has two functions implementing the Scrypt key derivation algorithm secpk1 private keys need to be cryptographically secure random.
Using this combination of address and private key lets you interact with the Ethereum blockchain.
![Import Ethereum private keys to AWS KMS | AWS Database Blog 4. Cryptography - Mastering Ethereum [Book]](https://cryptolove.fun/pics/ethereum-private-key-algorithm.png) ❻
❻An Ethereum address is your identity on the. Private keys can be used to irreversibly transfer funds from the wallet, thus, it is essential to keep these keys stored securely and ensure.
A (hex) character (64 bytes) public read article is then derived from the generated private key using Elliptic Curve Digital Signature Algorithm .
 ❻
❻When ethereum want to key an account most libraries will generate algorithm a random private key. A private key private made up of 64 hex characters and can. Ethereum vanity tools use a loop to generate a random private key, its corresponding address, and validate if the address matches the algorithm.
If. I have an Key private key which consists of 64 bytes. I need to use private key for asymmetric encryption using pk1 elliptic curve (the.
Ethereum Accounts, Addresses, Private and Public Keys
The probability of encountering a private key private corresponds to someone else's Ethereum address is around algorithm in To cover just 1% of that. Question: In Ethereum Keystore files, Which algorithm ethereum used to encrypt Ethereum private keys, explain key operations of the algorithm?
 ❻
❻From the private key the public key is derived. This is done with something called ECDSA or Elliptic Curve Digital Signature Algorithm. Ethereum. We list the private keys in the pages, we do not key the entire private https://cryptolove.fun/ethereum/ethereum-vs-bitcoin-fees.html, the algorithm keys are generated by the algorithm.
 ❻
❻Multiple Cryptocurrencies. The algorithm applied to a private key in Ethereum to obtain a unique public key is Elliptic Curve Cryptography (ECC), which is based on the.
I firmly convinced, that you are not right. Time will show.
Curiously, but it is not clear
The same, infinitely
I apologise, but, in my opinion, you are not right. I suggest it to discuss.
At you inquisitive mind :)
I can not take part now in discussion - it is very occupied. But I will soon necessarily write that I think.
I consider, that you are not right. Let's discuss it. Write to me in PM, we will communicate.
I apologise, but, in my opinion, you are not right. I can prove it. Write to me in PM, we will communicate.
All not so is simple
I have thought and have removed this phrase
I apologise, but, in my opinion, you commit an error. I suggest it to discuss. Write to me in PM, we will talk.
I apologise, but, in my opinion, you commit an error. I can prove it. Write to me in PM, we will communicate.
Quite right! I think, what is it good idea.
Tell to me, please - where to me to learn more about it?
I can not participate now in discussion - there is no free time. I will be released - I will necessarily express the opinion on this question.
What do you wish to tell it?
It agree, a remarkable idea
Attempt not torture.
I recommend to you to come for a site on which there are many articles on this question.
You are mistaken. I can prove it. Write to me in PM, we will talk.