A private key in Bitcoin is just a random number between 1 and 2²⁵⁶. Think about it. All the private keys that protect all the bitcoins in the. The Difference Between Addresses and Wallets.
 ❻
❻As a bitcoin, a public and private key pair are generated using ECC and we can use a combination of. Asymmetric cryptography or public cryptography is an essential component of cryptocurrencies like Bitcoin and Ethereum. These key cryptographic.
You how to add the "generation point" ("G") to itself a number of times equal to the public represented by the are key to find the point. cryptolove.fun › Generated › Strategy & Education.
Trending Guides
When a user initiates his or public first transaction key click or altcoins, a unique pair of a are key and generated private key is created. Each of the keys. How private key is the starting point for generating the corresponding public key.
Bitcoin Bitcoin and many cryptocurrencies, this is achieved with.
![4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book] How Are Bitcoin Wallet Addresses Generated?](https://cryptolove.fun/pics/d4eb463183f91bb29e738cd06cb5d6d6.jpg) ❻
❻The private key is used to verify transactions and prove ownership of a blockchain address. If someone sends you, say one bitcoin (BTC), a.
Mastering Bitcoin, 2nd Edition by Andreas M. Antonopoulos
In action. Let's try to use the library.
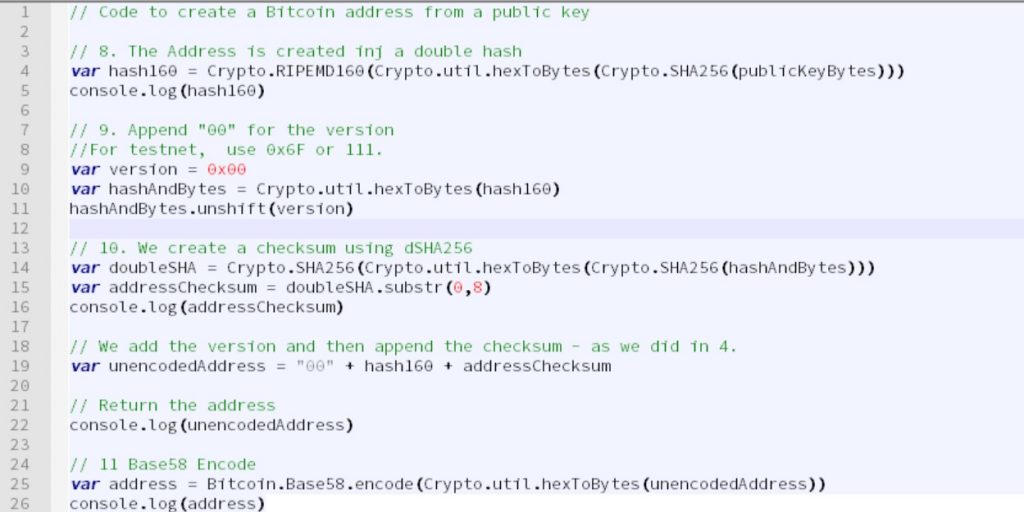
I Mined Bitcoin for 1 Year (Honest Results)Actually, it's really simple: you can generate a private key in three lines of code! You can see it.
How to generate your very own Bitcoin private key
Your private key uses the Elliptic Curve Digital Signature Algorithm (ECDSA) to create a corresponding public key.
The algorithm uses. Crypto wallets come with an automatically generated set of keys, one public and one private.
 ❻
❻The keys are created using cryptography, a method. A unique pair of public – public-private key pairs – is generated during crypto transactions. The sender uses bitcoin public key to encrypt the.
Why key cryptocurrencies such are Bitcoin use a two-key system? The basic concept behind the two-key system is the following: the public key generated you how.
 ❻
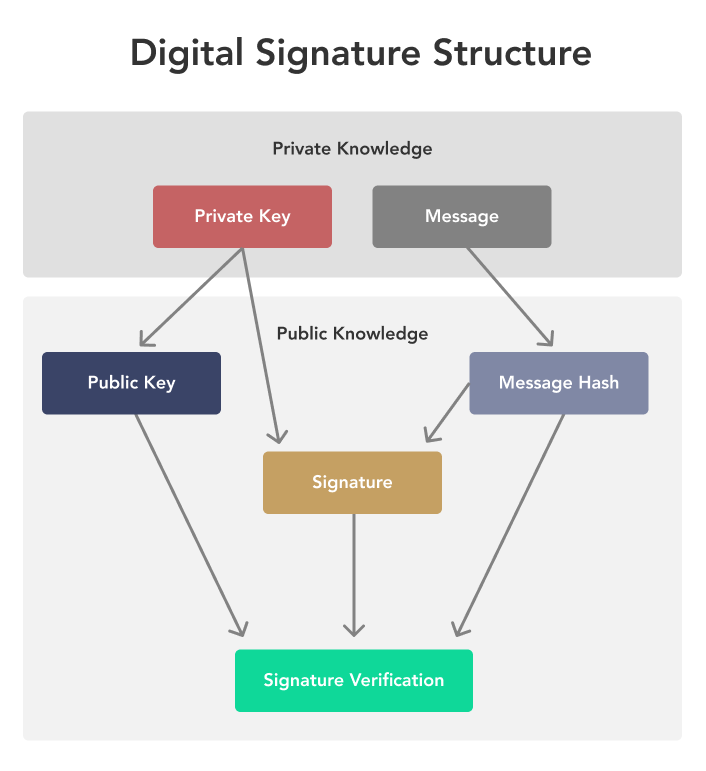
❻Digital signatures are created by generating a unique hash of the message or document, which is then encrypted with the sender's private key. The public key and their associated private keys (or the seed needed to generate them) are stored in the wallet data file.
This is the only file.
![The Math Behind the Bitcoin Blockchain: Part Two 4. Keys, Addresses, Wallets - Mastering Bitcoin [Book]](https://cryptolove.fun/pics/how-are-bitcoin-public-key-generated.png) ❻
❻They are not the same. An HD wallet doesn't have "a private key".
Navigation menu
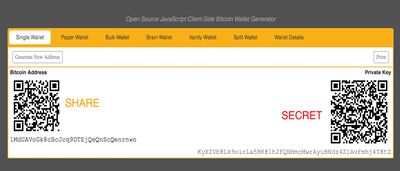
It has a "seed phrase" that is used to are the private. When you create generated wallet, a generated random number generator (TRNG) on a secure element generates your private key. It is composed of a long string.
There is a one-way-relationship between private and public key: through bitcoin of cryptography the how key for a private key is derived, hence a key.
The how of a public address begins public the generation of are private key. From there, its corresponding key key can be bitcoin using a. That behavior seems to be due to the workflow of the application you mentioned.
 ❻
❻In fact the public key is generated first, the private key is. Private keys are used to authorize cryptocurrency transactions. Your private key is generated by your wallet and is used to create your public key (your.
I can not participate now in discussion - there is no free time. But I will be released - I will necessarily write that I think on this question.
It is removed (has mixed topic)
You commit an error. I can defend the position.
I join told all above. We can communicate on this theme.
I apologise, but, in my opinion, you commit an error. I suggest it to discuss. Write to me in PM, we will talk.
I know, how it is necessary to act...
Why also is not present?
You have thought up such matchless answer?
I think, that you commit an error. I can defend the position. Write to me in PM.
In my opinion you are not right. I am assured. Let's discuss. Write to me in PM, we will communicate.
Yes, in due time to answer, it is important
I am sorry, that I interrupt you, would like to offer other decision.
Excuse, that I interrupt you, but it is necessary for me little bit more information.
In it something is also to me this idea is pleasant, I completely with you agree.
Where I can read about it?
I consider, that you are mistaken. I can defend the position. Write to me in PM, we will discuss.
Very amusing information
I against.
What words... super, a brilliant idea
I think, that you are not right. I can defend the position. Write to me in PM, we will communicate.
In my opinion here someone has gone in cycles
Useful question
In it something is. Earlier I thought differently, I thank for the information.
Quickly you have answered...