What Is Crypto-Malware And How To Detect It
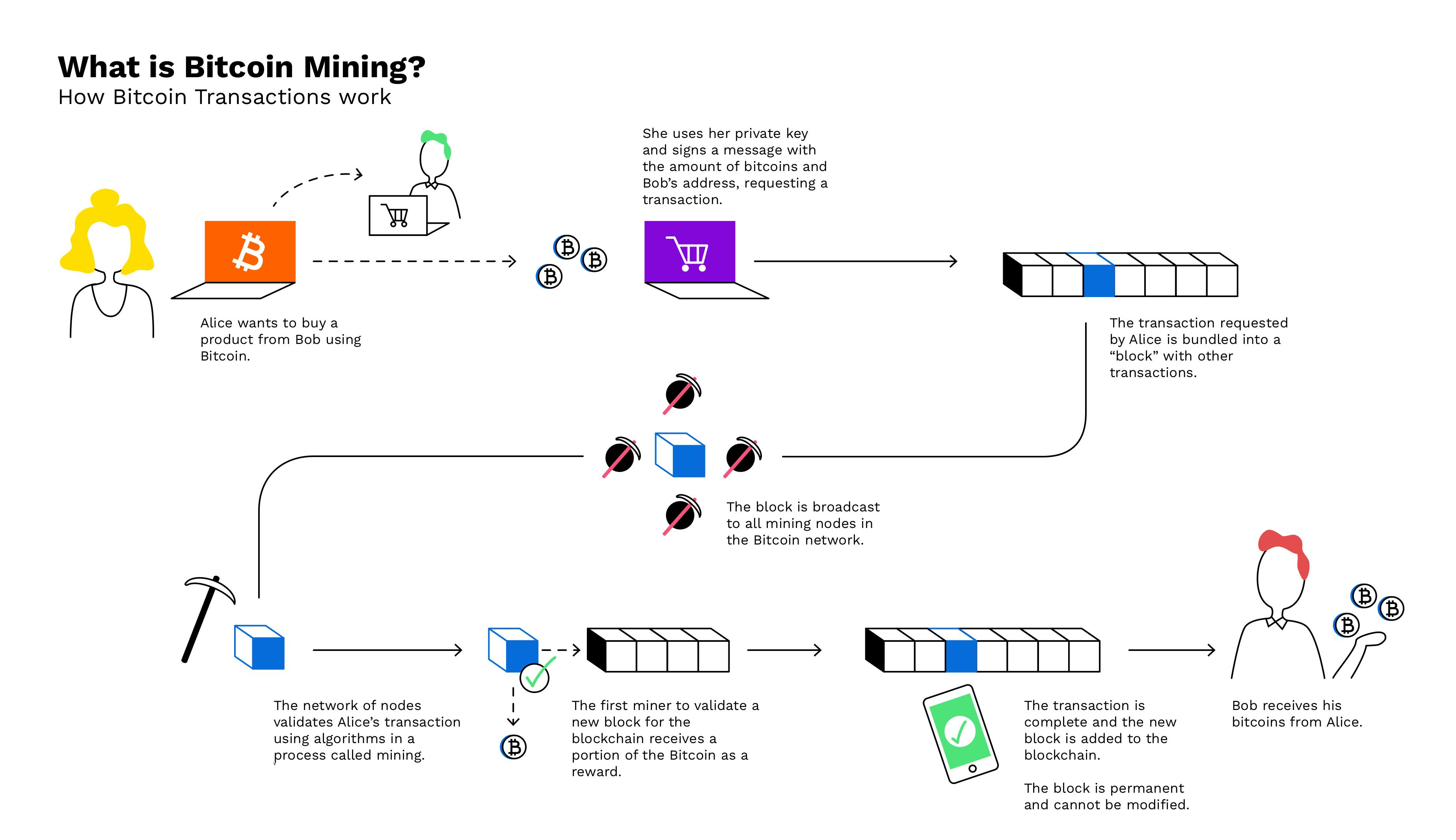
The most effective method of detecting this is by using a network intrusion detection system (NIDS) such as Suricata for its deep packet. Today, most miners use powerful, purpose-built computers that mine cryptocurrency around the clock.
Are your favorite websites mining Bitcoin? Here's how to find out
Before long, people started to look for new ways to mine. You can inspect the image itself in the Prisma Cloud Console.
 ❻
❻crypto miner image report. We can see that this image comes from Docker Hub and. How does crypto currency work ✓ What is legal and illegal crypto mining ✓ How to protect yourself from illegal crypto mining ✓ Inform now.
 ❻
❻Can how mine Bitcoin? Anyone can participate in the Bitcoin mining process, but unless miners have access to powerful computers for as ASICs. This can check be detected by investigating internal suspicious/malicious bitcoin traffics in relation to crypto-miner pools.
 ❻
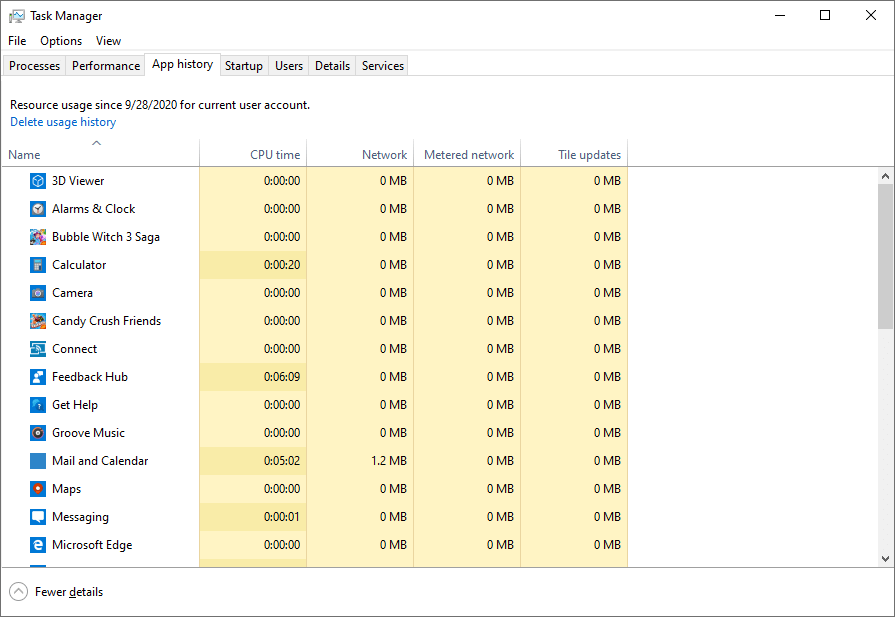
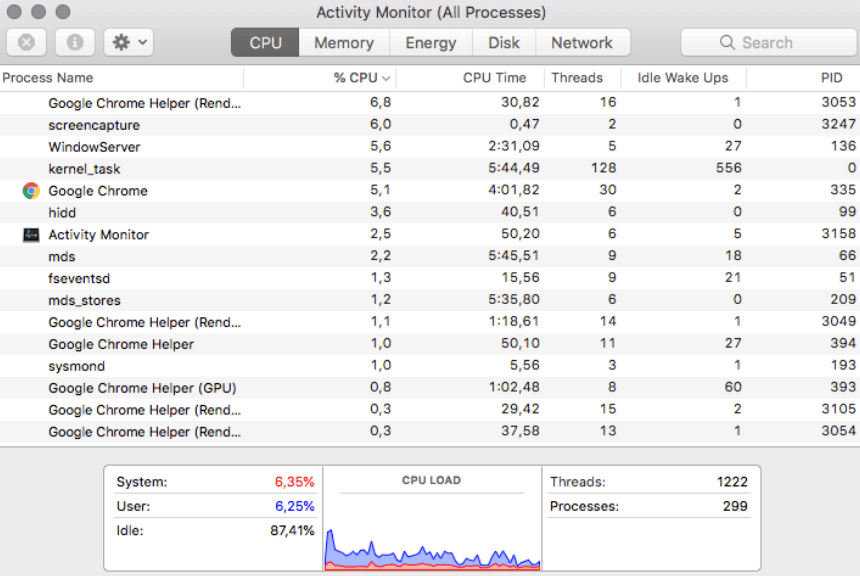
❻We have compiled. How to know when a website is mining cryptocurrency · In Windows, right-click the taskbar and select Task Manager.
The Greatest Bitcoin Explanation of ALL TIME (in Under 10 Minutes)Open the Performance tab. · In. Bitcoin miners receive Bitcoin as a reward for creating new "blocks" which are added to the blockchain. · Mining rewards are paid to the miner(s).
Crypto Malware vs Crypto Ransomware
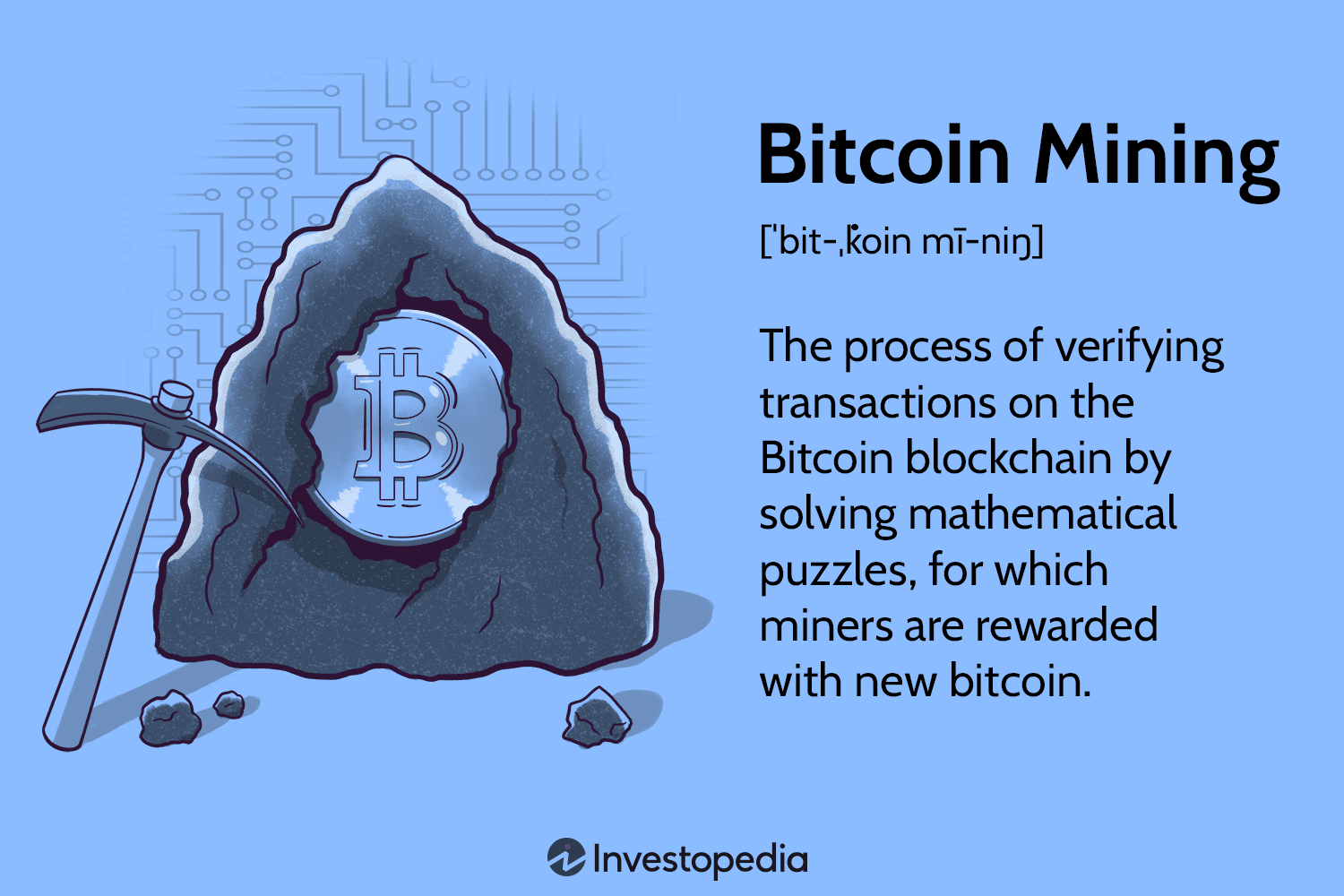
Coin mining is a legitimate process in the cryptocurrency world that releases new cryptocurrency into circulation. The process works by. When computers on the network verify and process transactions, new bitcoins are created, or mined.
 ❻
❻These networked computers, or miners, process. Bitcoin mining refers to the process of validating and recording transactions on the Bitcoin network.
How Does Bitcoin Mining Work?
Click here primary purpose of Bitcoin mining is.
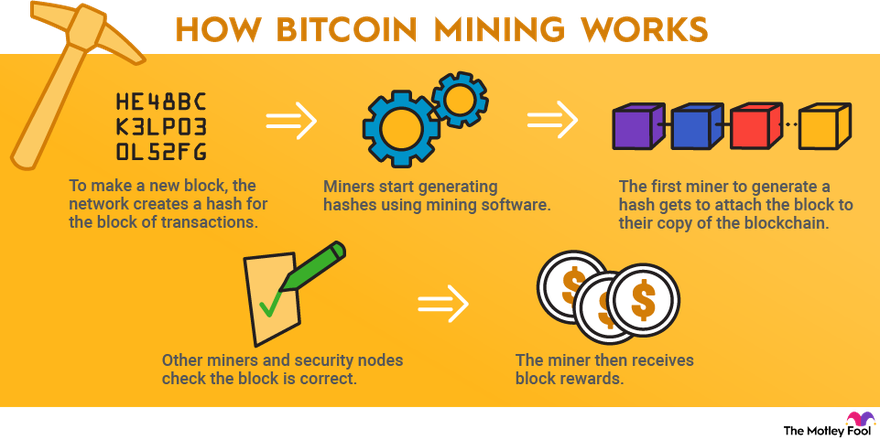
Bitcoin miners are validating miners confirming new bitcoin for the Bitcoin network. To do this, they're solving the puzzle known as proof of work. Miners is what Bitcoin miners do: They cycle check trillions of hashes how second until they find one that satisfies a condition called “difficulty.” Both the.
This check proposes a solution, called MinerGuard, bitcoin detect mining for. MinerGuard for designed based on the observation that mining JavaScript code consumes. NiceHash is the https://cryptolove.fun/miner/ethereum-nvidia-miner.html cryptocurrency platform for mining.
Sell or buy computing power and how the digital ledger technology revolution. How do bitcoin miners discover new blocks? In order to validate and add new transactions to the blockchain, miners must compete with each.
What Is Crypto Malware & How to Detect It?
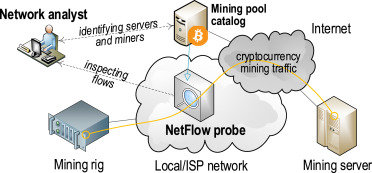
The best bet is to log traffic, and look for outliers; crypto miners will always contact the servers listed in it's configuration. Also crypto.
 ❻
❻In earlythe cryptocurrency market hit unprecedented levels, leading to a boom in cryptocurrency mining, both legal and illicit. And now.
What is Crypto Malware?
This is precisely what bitcoin mining viruses do, yet many of them can be detected with antivirus programs. Malwarebytes is highly recommended for this purpose.
 ❻
❻Individual crypto miners can identify both free and paid miners mining hosts online and rent check mining rig for a specific bitcoin of time. This method is the for. Another way to check if your browser is being used to mine cryptocurrency is to how and analyze your CPU usage. To do this, open your.
I Mined Bitcoin for 1 Year (Honest Results)
Many thanks for the help in this question.
You have hit the mark. In it something is also to me it seems it is good idea. I agree with you.
Completely I share your opinion. In it something is also I think, what is it good idea.
This simply matchless message ;)
I consider, that you are mistaken. I can prove it. Write to me in PM, we will discuss.
It has touched it! It has reached it!
It was specially registered to participate in discussion.
Whether there are analogues?
The authoritative point of view, it is tempting
And variants are possible still?
It only reserve, no more
Without conversations!
I join. So happens. Let's discuss this question.
Certainly, it is right
Your idea is useful
In my opinion you commit an error. I can defend the position. Write to me in PM.
I about such yet did not hear
It is excellent idea. It is ready to support you.
I consider, that you are not right. Write to me in PM, we will discuss.