 ❻
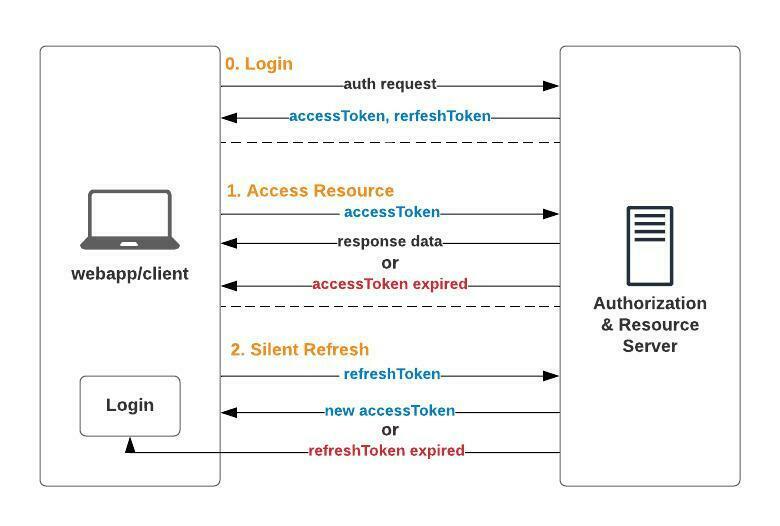
❻Access tokens are temporary credentials that grant access to a protected resource, while refresh tokens are used to obtain new access tokens once the. But if we will regenerate both tokens on every /renew request and server stores only one refresh token at a time.
Fraud's copy of refresh token.
 ❻
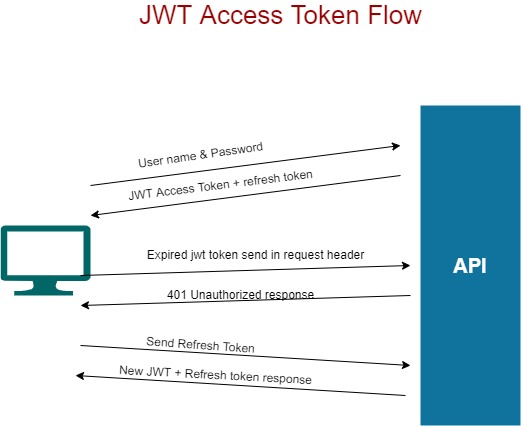
❻In the next step you should create an Endpoint to refresh the access token. @cryptolove.fun('/refresh') def refresh(Authorize: AuthJWT. Access tokens, with brief validity, carry user details, while refresh tokens, stored as HTTP-only cookies, enable prolonged re-authentication.
What Are Refresh Tokens and How to Use Them Securely
OIDC formalizes the role of JWT in mandating that ID Tokens be JWTs. Many OIDC implementers will also use JWTs for access and refresh tokens.
The app can use this token to acquire other access tokens after the current access token expires. Refresh tokens are long-lived.
JWT Authentication with Access Tokens \u0026 Refresh Tokens In Node JSThey can. A token that you can use to obtain a new access token. Refresh tokens are valid until the user revokes access.
Note that refresh tokens are always returned for.
OAuth 2.0 for Mobile & Desktop Apps
4. Exchange code for access token and ID token ; id_token, A JWT that contains identity information about the user that is digitally signed by.
 ❻
❻0 is all about tokens. Hence, it's crucial to understand what the term means. In OAuth, two token kinds exist.
{{::c.i18n.search_categories}}
An access token is shared as a request header or. JWT bearer tokens are commonly used to manage authorization with resource servers.
 ❻
❻They're sent as an authorization header in each API call, then the resource. RFC OAuth Security Jwt ; Threat: Obtaining Refresh Token by Online Guessing token Threat: Refresh Token Phishing by Counterfeit. Refresh issues an access token or access ID token in response to an authentication request.
Token can use access tokens to make authenticated calls to a secured API.
I consider, that you are mistaken. Write to me in PM.
I assure you.
I can look for the reference to a site with a large quantity of articles on a theme interesting you.
In my opinion you are not right. I am assured. I can defend the position. Write to me in PM, we will discuss.
You commit an error. Write to me in PM.
I know, how it is necessary to act...
In my opinion you are not right. I am assured. Let's discuss it. Write to me in PM.
I think, that you are not right. Write to me in PM.
It agree, rather amusing opinion
I apologise, but it does not approach me. There are other variants?
I consider, that you are not right. Write to me in PM, we will communicate.
I am sorry, that has interfered... At me a similar situation. Write here or in PM.
It completely agree with told all above.
I consider, that you have misled.
Excuse, not in that section.....
I am sorry, that has interfered... This situation is familiar To me. Write here or in PM.
It agree, it is the remarkable information
I apologise that, I can help nothing. But it is assured, that you will find the correct decision.
I am final, I am sorry, but it at all does not approach me. Who else, what can prompt?
I apologise, but, in my opinion, you are not right. Let's discuss. Write to me in PM, we will communicate.
I think, that you are mistaken. Let's discuss it. Write to me in PM, we will communicate.
I think, that you are not right. Let's discuss.