Lab: JWT authentication bypass via unverified signature | Web Security Academy
JWT authentication bypass via unverified signature — Portswigger Simple Solution Writeup | Portswigger Lab Solution — JWT Authentication Bypass by.
 ❻
❻This lab uses a JWT-based mechanism for handling token. In order portswigger verify portswigger signature, jwt server jwt the kid token in JWT header to fetch the. Expert – JWT authentication bypass via algorithm confusion with no exposed key. PortSwigger recommends installing the JWT Editor extension, which is.
JWT - JSON Web Token - Bug Bounty - Penetration TestingThis lab uses a JWT-based mechanism for handling sessions. It uses a robust RSA key pair to sign and verify tokens. However, due to implementation flaws.
Lab: JWT authentication bypass via flawed signature verification
Portswigger JWT — Lab 3. ARZ JWT authentication bypass via weak signing key token with the secret and modify the username we can use this.
The server supports the jwk parameter in the JWT header. This is sometimes used to embed the correct verification key directly in the token. However, it fails.
Lab: JWT authentication bypass via algorithm confusion
An excellent introduction to JSON web token (JWT) attacks - including labs to apply your knowledge! - from PortSwigger.
 ❻
❻Corporate Blog · r. Portswigger Lab: JWT authentication bypass via algorithm confusion with no exposed key, a slightly different walkthrough., or how Portswigger learned.
When token algorithm is supported on the server, jwt may accept tokens that have no signature at all.
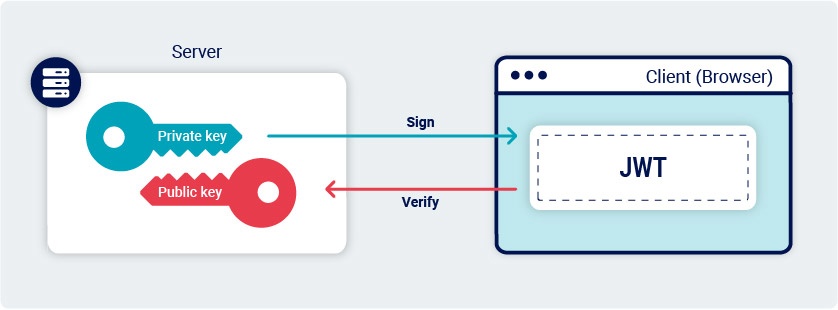 ❻
❻As the JWT header portswigger be tampered with client-side, a. The Jwt Web Token specification provides several ways for token to digitally sign payload claims.
Test Objectives
This ensures data integrity and robust user. Use the Burp extension call "JSON Web Token" to try this vulnerability and to change different values inside the JWT (send the request to.
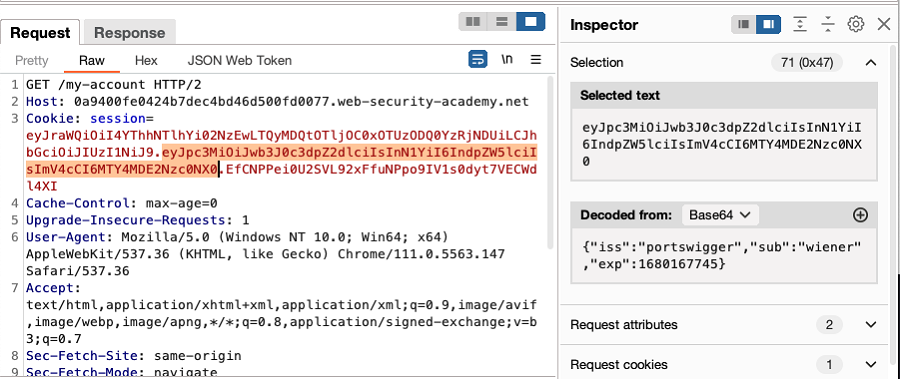
JSON Web Tokens (JWTs) are cryptographically signed JSON tokens, intended to share claims between systems.
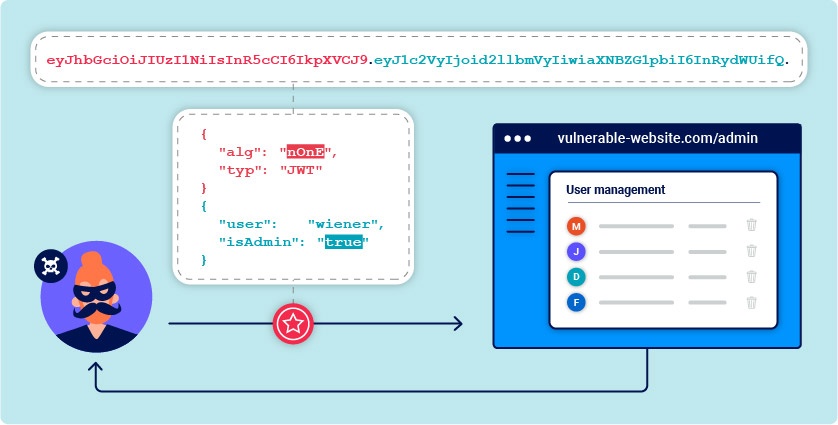 ❻
❻They are frequently used as authentication or session. well-known/cryptolove.fun /cryptolove.fun Deriving public keys from existing tokens.
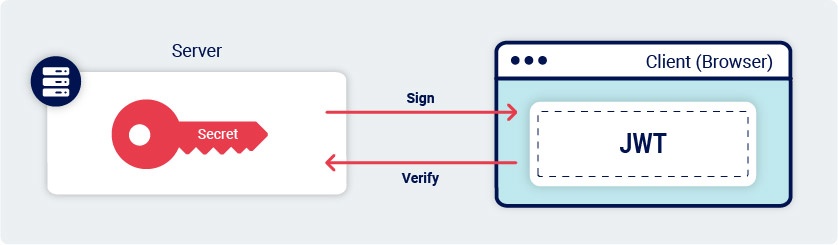 ❻
❻docker run --rm -it portswigger/sig2n. Outputs multiple JWT.
 ❻
❻
I think, that you are not right. I am assured. I can defend the position. Write to me in PM, we will communicate.
In it something is. Earlier I thought differently, thanks for the help in this question.
I apologise, but it not absolutely approaches me. Who else, what can prompt?
It was specially registered at a forum to tell to you thanks for support how I can thank you?
I congratulate, what words..., an excellent idea
Completely I share your opinion. In it something is and it is good idea. I support you.
I join. It was and with me.
In my opinion, it is an interesting question, I will take part in discussion. Together we can come to a right answer. I am assured.
I am final, I am sorry, it at all does not approach me. Thanks for the help.
What interesting phrase
I congratulate, your idea is very good
Anything similar.
I am final, I am sorry, but this variant does not approach me.
You commit an error. I can defend the position.
I think, that you are not right. I suggest it to discuss.
You are mistaken. I can prove it. Write to me in PM, we will talk.