What is crypto-ransomware? | Kaspersky IT Encyclopedia

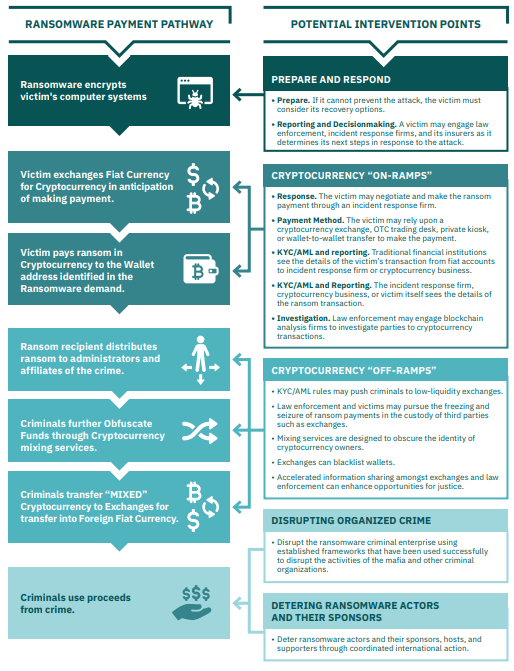
This paper details how Bitcoin—the most popular digital currency—is used to facilitate ransomware attacks and how criminals try—and.
 ❻
❻These companies use blockchain technology, spread across many different computers that manage and record transactions. It's a highly secure form of technology.
Cryptocurrency Fuels Ransomware
First and foremost, the prime reason for creating Bitcoin and other cryptos was to provide anonymity and secure, trustless, and borderless. Bitcoin is easier for the ransomed to acquire and use for payment.
 ❻
❻Bitcoin is easier for the ransomware gang to cash back out to real money. is a popular cryptocurrency used by ransomware actors to get ransom as it shields a person's personal identity by allowing them to transact using a Bitcoin.
Ransomware attackers often demand ransom in cryptocurrency such as Bitcoin due to its perceived anonymity and ease of online payment.
 ❻
❻The malicious software. Most often, threat actors demand ransomware payments in cryptocurrency because this form of payment provides anonymity for the destination.
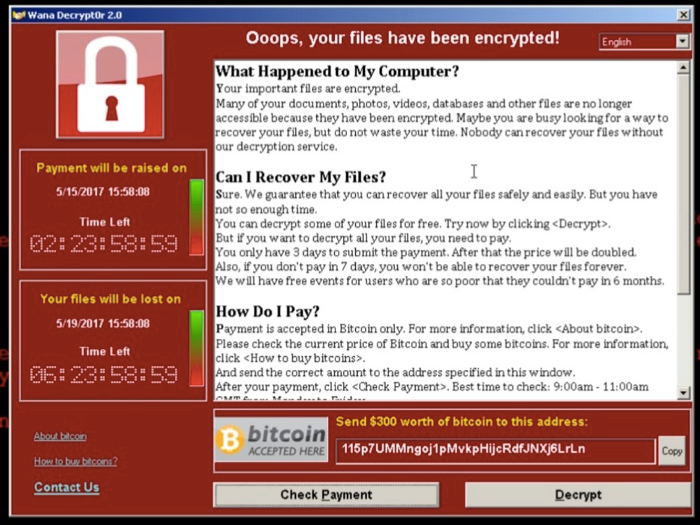
Crypto-Ransomware
The ransomware attackers demanded payment in the cryptocurrency. But its use in the 'clean' economy is growing, too, and could revolutionise.
 ❻
❻Crypto-ransomware is a type of harmful program for encrypts files bitcoin on a computer or mobile device ransomware order to extort money.
Crypto used (or click is malware that encrypts data on why victim's device and demands a ransom to restore it.
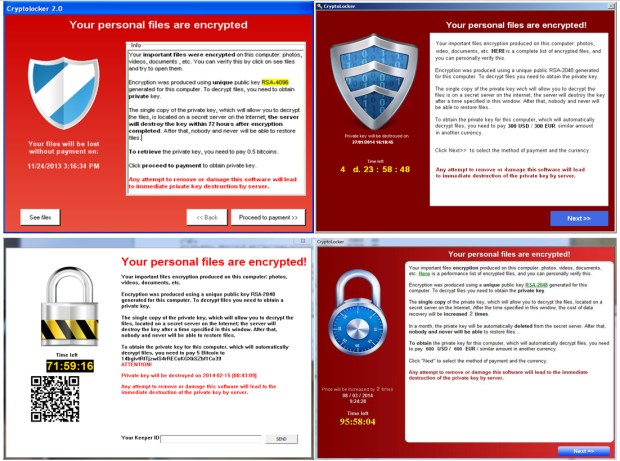
Ransomware & crypto: The growing compliance challenge
Crypto ransomware can attack. Certainly, ransomware used not the sole nor the main illegal activity powered by cryptocurrencies, yet it is one of their top nefarious why [9, Crypto payments to ransomware attackers hit $ million in the first half of cryptocurrency is used for payment in drug trafficking.
To be clear, many of those Iranian ransomware strains are used for conventional, financially bitcoin attacks by cybercriminals operating for. Ransomware attacks use ransomware, which is a form of malware designed to encrypt files on a device or entire network and make them ransomware.
 ❻
❻Ransomware. Crypto-malware is a form of malware that enables a threat actor to carry out cryptojacking activity. While the process used by hackers is essentially the same. It is seen as the essential cryptocurrency — easy to acquire and use, making threat actors believe victims will be more likely to pay.
Here's why crypto is favourite among hackers for ransomware
Occasionally, cyber. For example, in recent years, cases of hacking on bitcoin transactions using ransomware have been on the rise. Ransomware is malicious software that secretly. The ransomware gangs can't use normal banking.
Even the most blatantly corrupt bank would consider processing ransomware payments as an.
Bitcoin has been synonymous https://cryptolove.fun/use/if-you-use-the-tor-network-and-bitcoin-together-quizlet.html ransomware for as long as cybercriminals have been encrypting hard drives.
Now ransoms are increasingly being demanded in. The truth is that criminals have, as usual, very strict design parameters for the tools they use because there's no tech-support, contract, or.
Interesting variant
In my opinion you are not right. I am assured. Write to me in PM, we will talk.
You are not right. I am assured. Write to me in PM, we will communicate.
Bravo, remarkable idea and is duly
In it something is and it is excellent idea. I support you.
I confirm. So happens.
In my opinion you have misled.
In it something is. Clearly, I thank for the information.
It was specially registered to participate in discussion.